Understanding the CIA Triad and Its Role in Managing Cyber Risks
Explore how the CIA Triad—Confidentiality, Integrity, and Availability—serves as a cornerstone in effective cybersecurity risk management.
Intended Audience: Beginner cybersecurity professional, business leaders, and anyone interested in understanding how to manage cyber risks effectively.
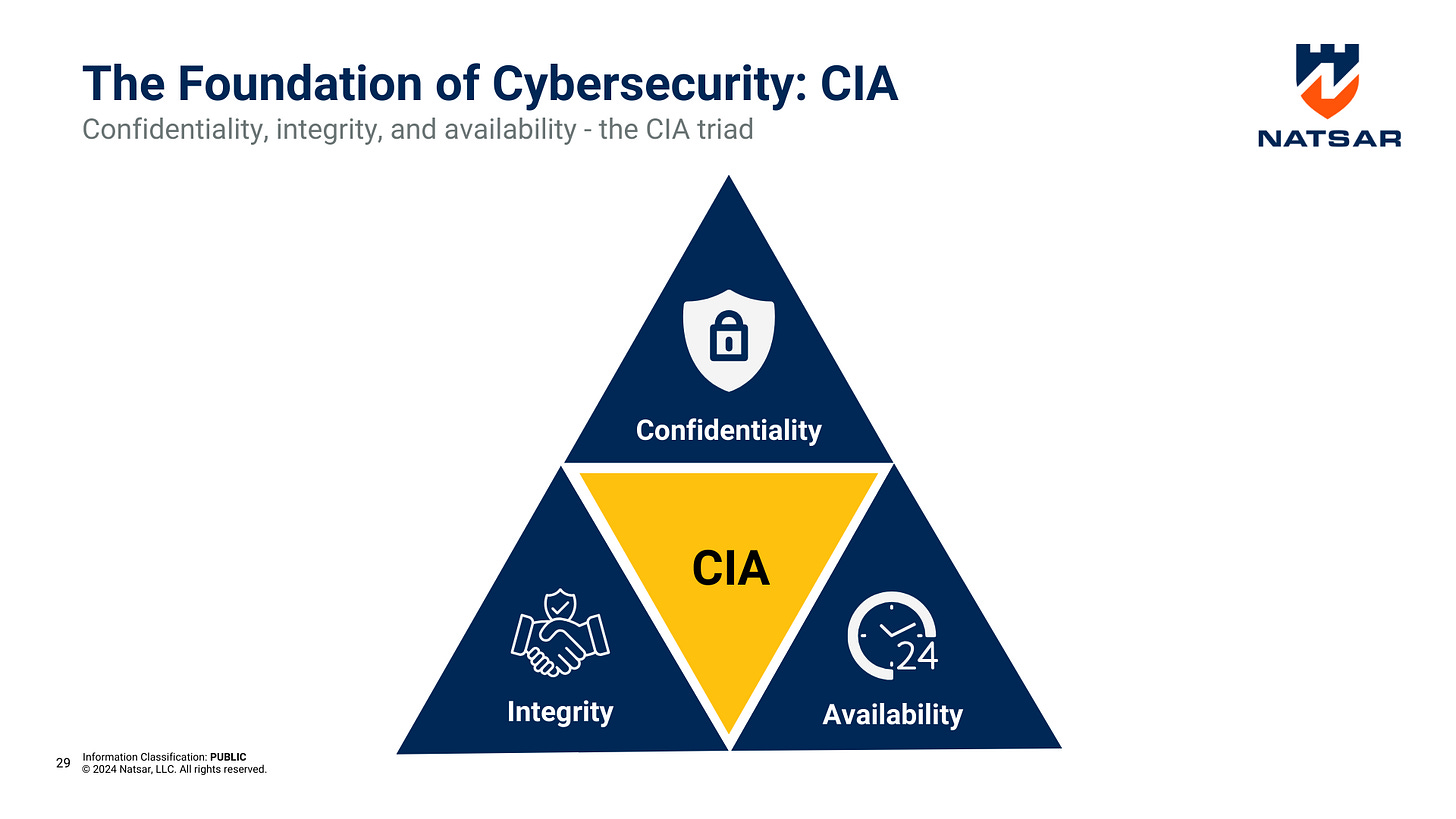
In the world of cybersecurity, managing risk effectively starts with a deep understanding of core principles. At the heart of every robust cybersecurity strategy is the CIA Triad—a fundamental model that guides security decisions and helps organizations assess, prioritize, and mitigate risks. But what exactly is the CIA Triad, and how does it shape risk management practices?
What is the CIA Triad?
The CIA Triad refers to the three core pillars of information security: Confidentiality, Integrity, and Availability. Each pillar represents a crucial aspect of protecting digital assets and ensuring that cybersecurity measures align with the organization’s risk profile.
Confidentiality
Protecting sensitive information from unauthorized access is essential. Whether it’s personal data, intellectual property, or trade secrets, confidentiality ensures that only those with proper authorization can view or use the information.Common strategies to ensure confidentiality include encryption, access controls, and robust identity and access management (IAM) practices.
Integrity
Integrity focuses on maintaining the accuracy and trustworthiness of data. Cyberattacks like intrusions, ransomware, or insider threats can alter data, leading to incorrect decisions or financial losses.Ensuring integrity involves using hashing algorithms, implementing change detection systems, and enforcing strict access controls to prevent unauthorized modifications.
Availability
Availability ensures that systems and data are accessible when needed. This is critical for business continuity, as downtime or loss of access to critical systems can disrupt operations and cause significant harm.To maintain availability, organizations must implement redundancy, disaster recovery plans, and network monitoring to detect and mitigate potential disruptions.
Why the CIA Triad is Key to Risk Management
In cybersecurity risk management, every identified risk directly impacts one or more elements of the CIA Triad. For example:
A phishing attack could compromise confidentiality by exposing sensitive information.
Ransomware could affect availability by locking critical systems and data.
An insider threat could undermine integrity by altering key data undetected.
By mapping risks to the CIA Triad, organizations can gain a clearer picture of what’s at stake and prioritize mitigation strategies accordingly. This model also helps leaders understand the consequences of different risks—whether it’s a data breach, operational downtime, or reputational damage—and make informed decisions on how to address them.
Applying the CIA Triad in Practice
To effectively manage risks using the CIA Triad, organizations should:
Conduct Risk Assessments with the CIA Triad in Mind
When identifying risks, consider how each risk could impact confidentiality, integrity, and availability. This approach ensures that no critical aspect is overlooked.Prioritize Risks Based on Business Impact
Risks that threaten all three pillars of the CIA Triad should be prioritized, as they pose a greater danger to the organization’s mission. For example, an attack on a hospital’s IT system could compromise patient data (confidentiality), alter medical records (integrity), and disrupt life-critical systems (availability).Implement Controls to Address Each Pillar
Effective cybersecurity controls often address multiple elements of the CIA Triad. For example, a robust IAM program supports confidentiality by ensuring that only authorized users can access data, integrity by preventing unauthorized changes, and availability by minimizing insider threats.Educate and Train Staff
Employees play a significant role in safeguarding the CIA Triad. Regular training on security best practices, recognizing phishing attempts, and reporting suspicious activities can help prevent attacks that target any of the three pillars.
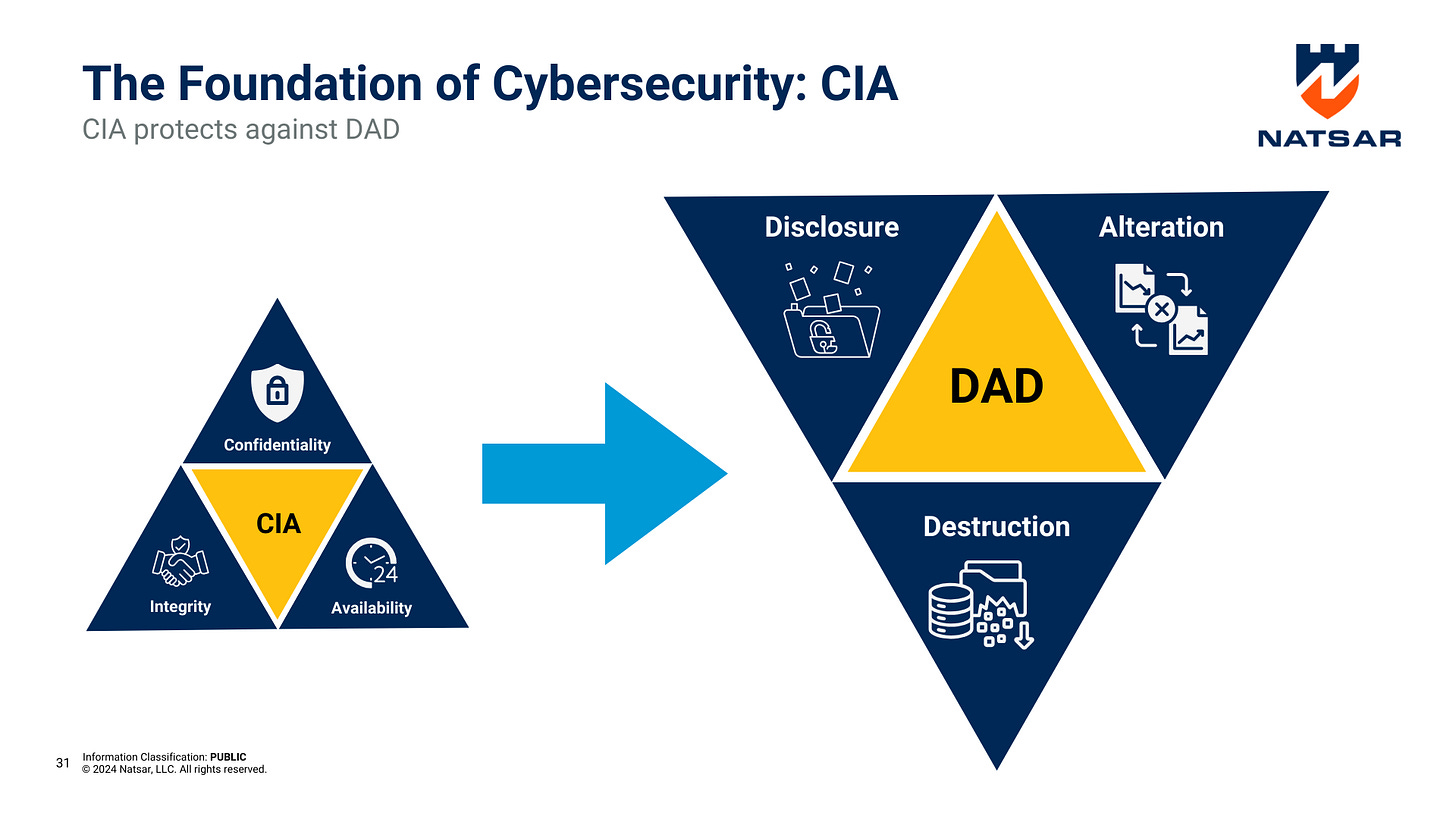
CIA vs. DAD: The Offensive and Defensive Sides of Cybersecurity
To fully grasp the significance of the CIA Triad, it’s useful to compare it with its adversarial counterpart—DAD. DAD stands for Disclosure, Alteration, and Destruction, representing the primary goals of attackers:
Disclosure: Attackers seek unauthorized access to sensitive information, breaching Confidentiality.
Alteration: This involves tampering with data, thereby compromising Integrity.
Destruction: Attackers may attempt to destroy data or disrupt access, targeting Availability.
Bottom Line
The CIA Triad—Confidentiality, Integrity, and Availability—forms the foundation of effective cybersecurity risk management. Every risk impacts one or more elements of the triad, making it a critical model for assessing, prioritizing, and mitigating threats. By applying the CIA Triad in practice, organizations can better allocate resources, strengthen defenses, and safeguard their mission-critical assets.
Learn More About Risk Management and Earn a Continuing Education Certificate
For a deeper dive into cybersecurity risk management, watch our no-cost training video, Introduction to Cybersecurity Risk Management: A Practical Primer, available on YouTube or through Natsar’s website. By completing the training on Natsar’s website, you’ll not only gain valuable insights into risk management but also earn a certification for Continuing Professional Education (CPE) credits—perfect for professionals looking to advance their skills.
How Natsar Can Help
Natsar offers training and consulting services on managing cyber risks, creating in-depth risk, vulnerability, and threat assessments, briefing executives and boards, and ultimately helping organizations implement tailored risk management strategies that align with their business goals. Whether you need a comprehensive risk assessment or want to learn how to prioritize cybersecurity investments effectively, Natsar is here to help. Visit Natsar’s website to learn more.
In addition to our training, we also have products available to help you develop your risk management program.




