Risk Assessments for Cybersecurity: Frameworks, Insights, and Best Practices
Explore essential cybersecurity risk assessment frameworks, key sources of risk, and actionable best practices to help your organization prioritize and mitigate threats effectively.
Intended Audience: Beginner cybersecurity professional, business leaders, and anyone interested in enhancing their cybersecurity program.
Risk assessments aren’t just a box to check for compliance—they’re a vital tool for understanding the organization’s current security posture and identifying areas for improvement. By systematically evaluating potential threats, vulnerabilities, and the likelihood of exploitation, businesses can make informed decisions about how to allocate resources and mitigate risk.
Cybersecurity threats evolve constantly, and without a structured risk assessment process, organizations may overlook critical risks or misallocate resources to low-priority areas. Regular assessments provide a clearer picture of the organization’s most pressing vulnerabilities, ensuring that leaders can focus on protecting what matters most—whether it’s sensitive customer data, critical infrastructure, or intellectual property.
Why Conduct a Cybersecurity Risk Assessment?
Cyber risks are constantly emerging, making it essential for organizations to stay ahead by identifying and prioritizing threats. A well-executed risk assessment helps:
Identify Vulnerabilities: Highlight weaknesses before they are exploited by attackers.
Prioritize Resources: Direct attention and budget to the highest-risk areas, ensuring efficient use of resources.
Support Compliance: Meet regulatory requirements by demonstrating a structured approach to risk management.
Enable Better Decision-Making: Provide leadership with actionable insights to guide cybersecurity investments.
Understanding Risk: Sources and Types
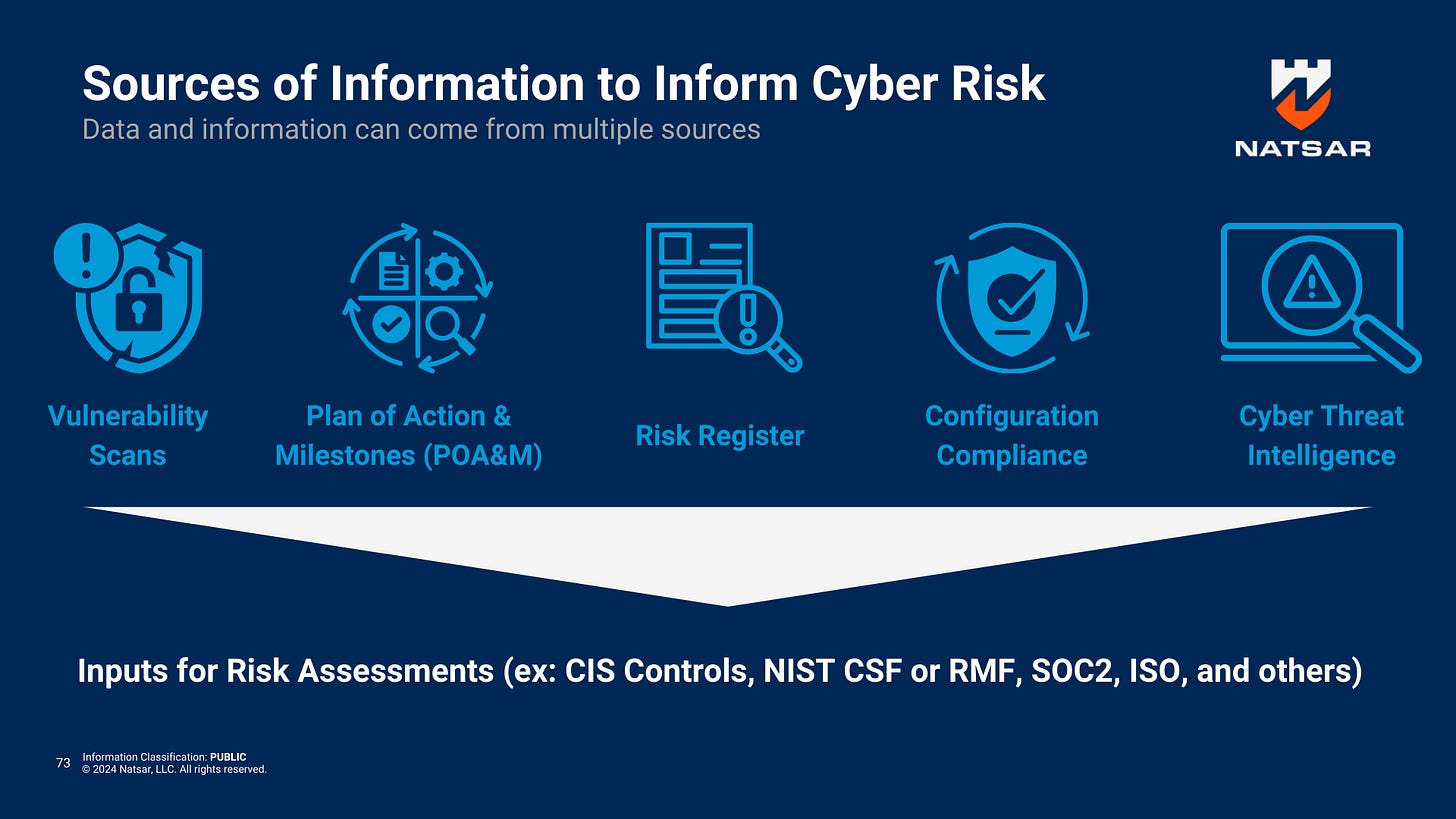
A thorough risk assessment involves analyzing multiple sources of risk. Common sources include:
Vulnerability Scanning: Automated tools can detect known vulnerabilities across systems and networks, but these findings must be prioritized based on exploitability and impact.
Threat Assessments: Evaluating potential threats specific to your industry or region, such as state-sponsored attackers, organized crime groups, or hacktivists.
Configuration Compliance and System Hardening: Ensuring that systems adhere to secure baseline configurations, reducing the attack surface.
Cyber Threat Intelligence (CTI): Leveraging CTI feeds to understand the latest tactics, techniques, and procedures (TTPs) used by attackers.
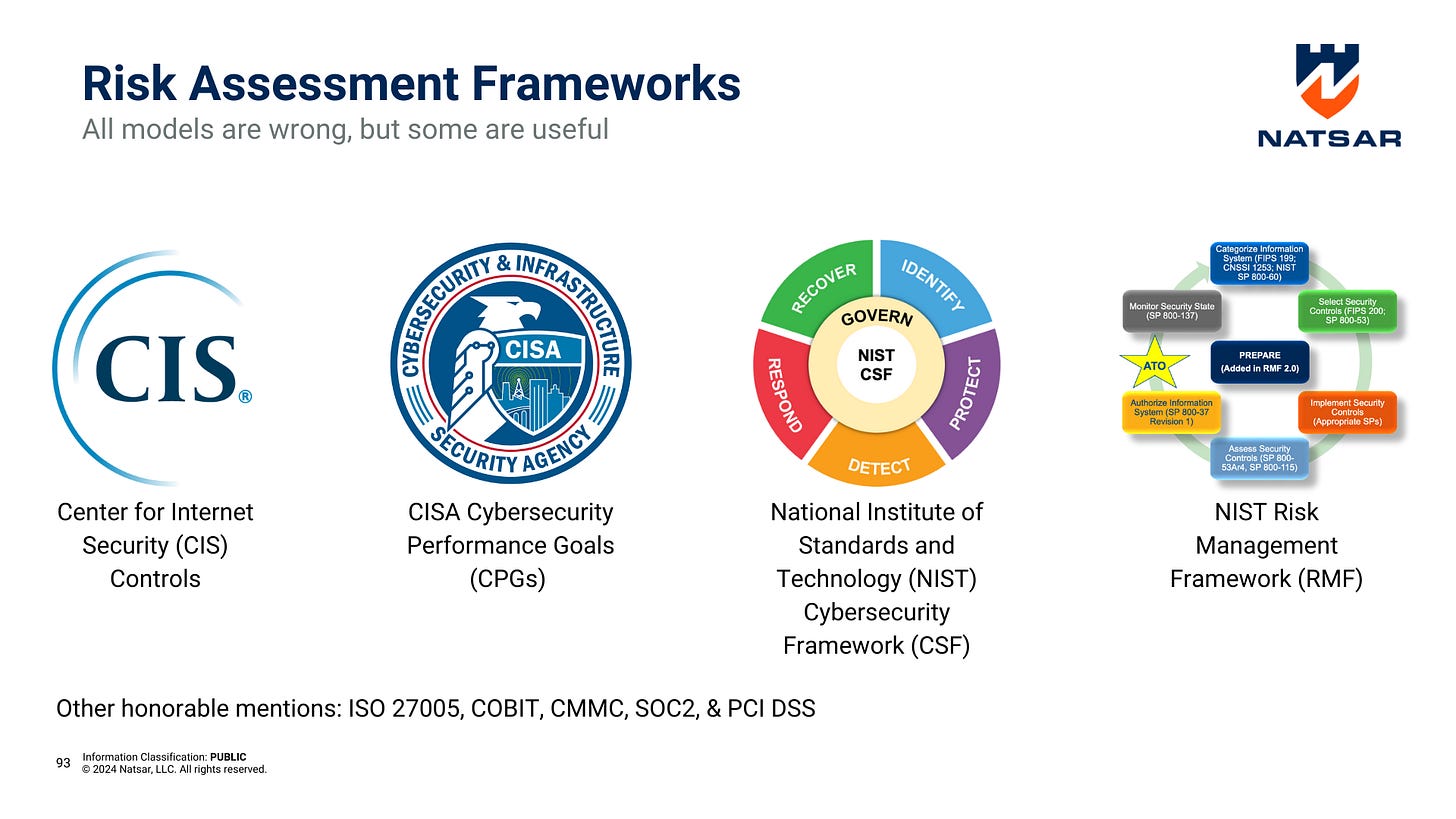
Popular Cybersecurity Risk Frameworks
Several well-established frameworks guide organizations in performing risk assessments. Selecting the right framework depends on your organization’s size, industry, and regulatory requirements. Key frameworks include:
CIS Controls: This framework offers prioritized, actionable best practices for cyber defense that has been adopted globally. The CIS Controls are particularly useful for organizations looking to implement effective, scalable security measures.
NIST Cybersecurity Framework (CSF): Widely adopted across industries, the NIST CSF helps organizations identify, protect, detect, respond to, and recover from cyber incidents. It emphasizes a continuous improvement approach to cybersecurity.
NIST Risk Management Framework (RMF): Designed specifically for federal agencies and contractors, NIST RMF provides a comprehensive approach to managing security and privacy risks across an information system’s lifecycle.
CISA Cybersecurity Performance Goals (CPGs): Aimed at critical infrastructure, the CPGs provide voluntary, outcome-driven goals to enhance cybersecurity posture.
Each framework emphasizes continuous improvement, ensuring that risk assessments are not a one-time activity but an ongoing process.
Best Practices for Conducting a Cybersecurity Risk Assessment
Conducting a cybersecurity risk assessment is not just about identifying threats and vulnerabilities; it's about creating a clear and actionable roadmap for improving security posture. One of the most valuable outcomes of a well-executed risk assessment is the development of both the “as-is” state and the “to-be” state of an organization’s cybersecurity program.
Define the As-Is State: The as-is state represents the current condition of the organization’s cybersecurity risk posture. This involves documenting existing controls, known vulnerabilities, identified risks, compliance gaps, and the overall maturity of the cybersecurity program. By establishing this baseline, organizations can understand where they stand today and measure future progress.
Establish the To-Be State: The to-be state reflects where the organization desires to be—or in many cases, where it must be to comply with industry regulations, internal policies, or applicable laws. This state outlines the desired level of cybersecurity maturity, specifying the necessary controls, mitigations, and improvements needed to achieve compliance and reduce risk to acceptable levels.
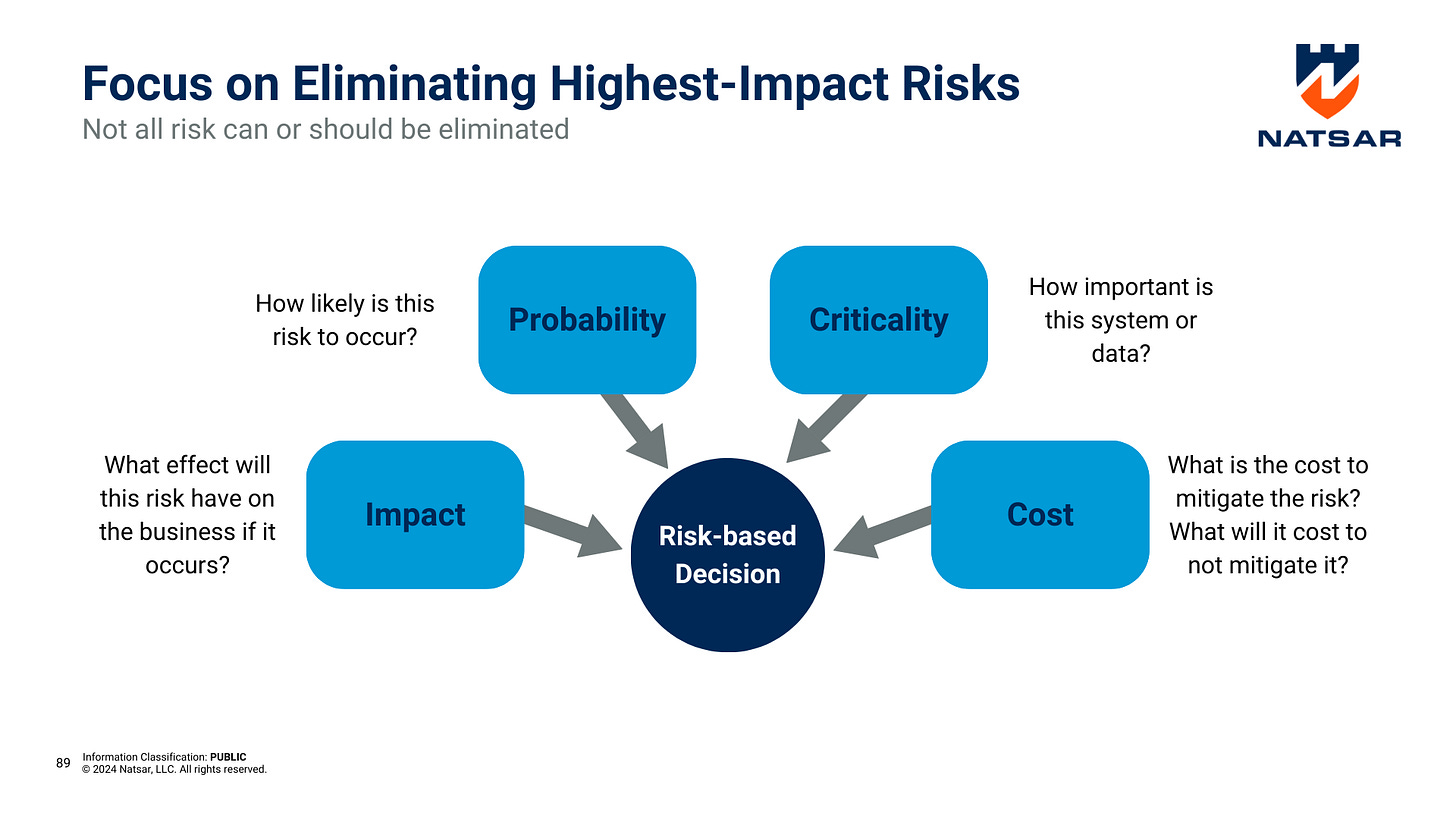
The gap between the as-is and to-be states provides a roadmap for prioritizing actions, setting realistic goals, and allocating resources effectively.
To maximize the value of your risk assessment, consider these best practices:
Focus on High-Impact Risks: Not all risks are created equal. Prioritize risks based on their potential impact, likelihood of occurrence, and cost of mitigation.
Engage Stakeholders: Involve key stakeholders from IT, legal, compliance, and business units to gain a holistic view of risks and ensure alignment with organizational goals.
Use Quantitative and Qualitative Methods: Combine quantitative methods (e.g., using metrics like CVSS scores) with qualitative insights from subject matter experts to get a balanced view of risks.
Leverage Automation: Use automated tools for vulnerability scanning, compliance checking, and threat intelligence, but validate findings with human analysis.
Maintain a Risk Register: Document identified risks, their potential impact, mitigation strategies, and status updates in a centralized risk register. This helps track progress and communicate risks to leadership. You can get a copy of Natsar’s risk register here.
Using Risk Assessment Output to Communicate with Executives
The output of a risk assessment serves as a critical tool for bridging the gap between cybersecurity teams and executive leadership. Effective communication ensures that executives not only understand the risks but also feel empowered to make informed decisions about risk mitigation and investment.
Risk Communication: Present risk assessment findings in terms of business impact—focusing on risks that could disrupt critical operations, damage the organization’s reputation, or lead to financial loss. Using straightforward, non-technical language helps executives grasp the urgency of key risks.
Prioritize by Business Impact: Highlight risks based on their potential impact on high-value assets, compliance obligations, and operational continuity. By tying risks to business priorities, executives can better understand where to allocate resources.
Justify Funding Requests: The gap analysis between the as-is and to-be states can be used to build a case for increased cybersecurity funding. Showing executives the cost-benefit of closing critical gaps helps in securing support for necessary improvements.
Regulatory Compliance: Risk assessment results are often used to demonstrate compliance with frameworks and regulations such as NIST, CIS Controls, or industry-specific standards. Communicating how the assessment aligns with regulatory requirements helps executives understand the importance of proactive security measures.
Bottom Line
A well-structured cybersecurity risk assessment is vital for any organization looking to manage its cyber risks effectively. By leveraging established frameworks, engaging stakeholders, and focusing on high-impact risks, organizations can build a proactive cybersecurity posture. Risk assessments are not just about identifying threats—they’re about understanding the bigger picture and making informed decisions to safeguard critical assets.
Learn More About Risk Management and Earn a Continuing Education Certificate
For a deeper dive into cybersecurity risk management, watch our no-cost training video, Introduction to Cybersecurity Risk Management: A Practical Primer, available on YouTube or through Natsar’s website. By completing the training on Natsar’s website, you’ll not only gain valuable insights into risk management but also earn a certification for Continuing Professional Education (CPE) credits—perfect for professionals looking to advance their skills.
How Natsar Can Help
Natsar offers training and consulting services on managing cyber risks, creating in-depth risk, vulnerability, and threat assessments, briefing executives and boards, and ultimately helping organizations implement tailored risk management strategies that align with their business goals. Whether you need a comprehensive risk assessment or want to learn how to prioritize cybersecurity investments effectively, Natsar is here to help. Visit Natsar’s website to learn more.
In addition to our training, we also have products available to help you develop your risk management program.


