Protect Your Network from Cyberattacks with Segmentation Strategies
Why Flat Networks Are a Security Risk and How Segmentation Enhances Cyber Defenses
Intended Audience: Entry-level cybersecurity professionals, IT administrators, and anyone responsible for securing corporate networks.
The Risks of Flat Networks
Many organizations unknowingly operate on what is called a flat network architecture—a network design where all devices and systems can freely communicate with one another. While this may simplify IT management, it also creates an enormous security risk by allowing attackers to move laterally across the environment once they gain initial access.
If a cybercriminal or malware infiltrates just one system, a flat network provides no barriers to prevent the attack from spreading. Ransomware, insider threats, and advanced persistent threats (APTs) all thrive in flat network environments where they can pivot from one compromised device to another without resistance. The more open your network is, the harder it becomes to contain an incident.
How Network Segmentation Reduces Risk
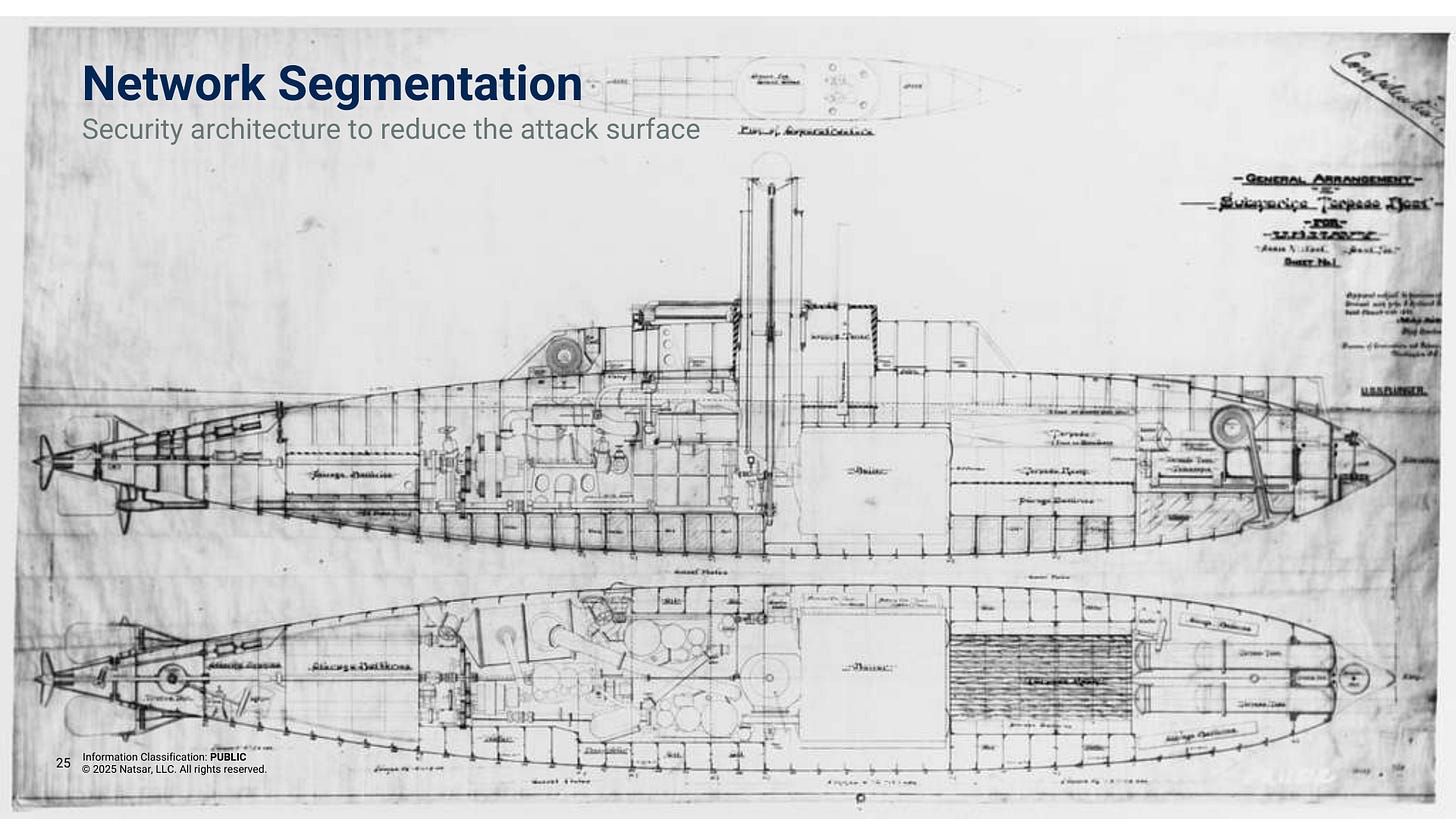
To understand why network segmentation is so effective, consider how ships are designed. Ships are built with watertight compartments that prevent the entire vessel from sinking if one section is breached. If water floods into one area, bulkheads keep it from spreading to other parts of the ship.
Now, think of your network the same way. A flat network is like a ship with no compartments—if one system is compromised, an attacker has free rein to move across your environment. Network segmentation acts like a series of bulkheads, limiting the spread of an attack and keeping critical assets safe.
By dividing a network into isolated sections, segmentation helps limit the impact of security breaches and reduces an organization’s overall attack surface.
Key Benefits of Network Segmentation
Prevents Lateral Movement – Just as bulkheads contain flooding, segmentation contains cyber threats, preventing them from spreading across the network.
Protects Critical Assets – Systems with sensitive data, such as financial records or customer information, remain isolated from general network traffic.
Improves Performance – By reducing unnecessary traffic, network segmentation enhances speed and efficiency for business-critical applications.
Enhances Compliance – Many regulations, including PCI DSS, HIPAA, CMMC, NIST 800-53 and others, require segmentation to protect sensitive data.
Limits Insider Threats – Users only have access to the data and systems necessary for their job roles, reducing the risk of internal breaches.
Types of Network Segmentation
Physical Segmentation
This involves separating networks using different physical hardware, such as switches, routers, and firewalls. This is the most secure form of segmentation but can be costly and complex to implement at scale.
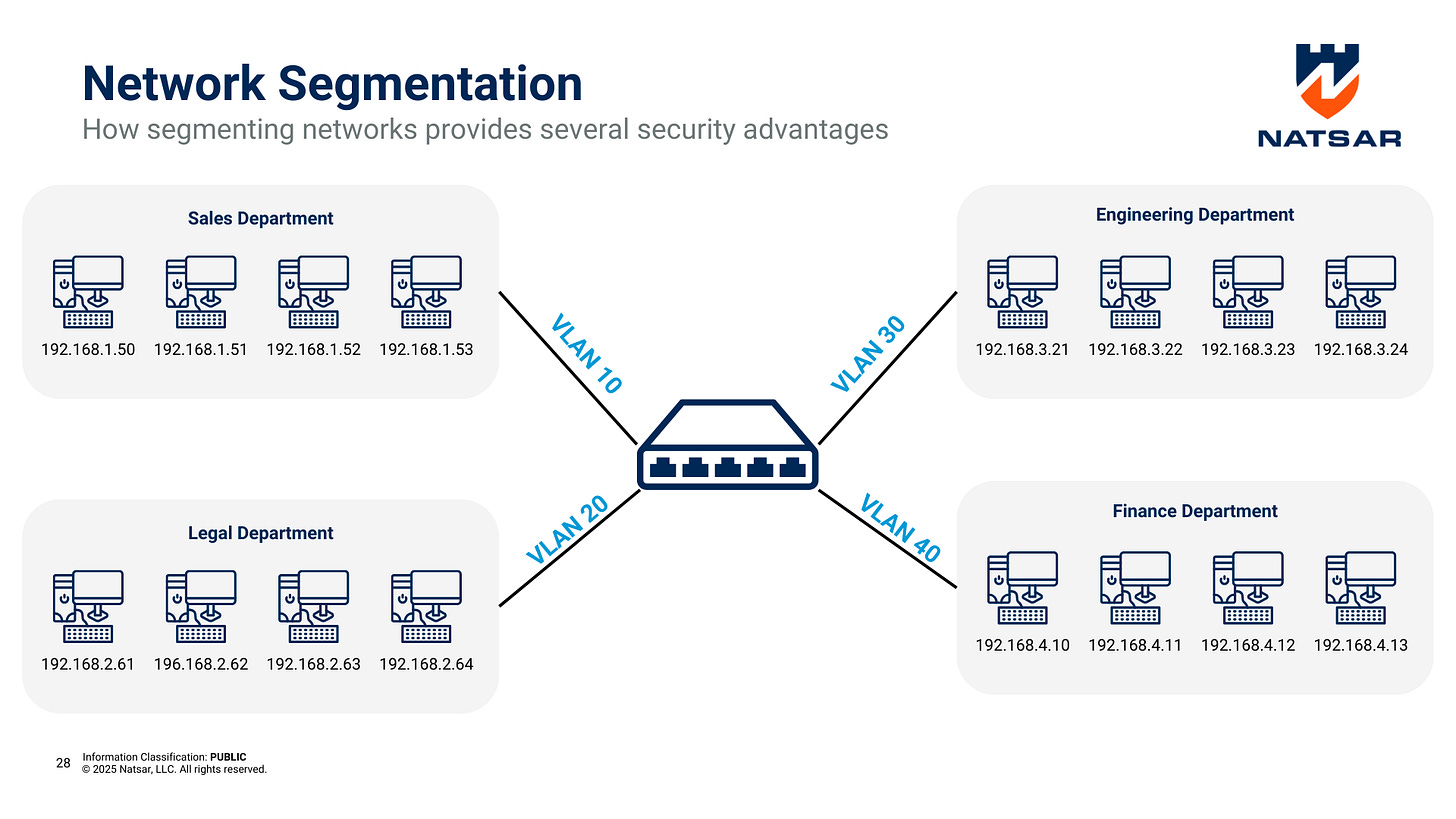
Virtual Local Area Networks (VLANs)
VLANs logically divide a network into isolated segments without requiring separate physical infrastructure. VLANs are widely used in enterprise environments to group devices based on function, such as separating IoT devices from internal workstations.
Microsegmentation
Microsegmentation applies granular access control policies down to individual workloads or applications. This is commonly used in cloud environments and software-defined networking (SDN) to provide zero trust access controls.
Air-Gapped Networks
An air-gapped network is completely isolated from the internet and other networks, typically used in highly sensitive environments, such as military, financial, and industrial control systems.
Best Practices for Implementing Network Segmentation
✅ Identify Critical Systems – Prioritize segmentation for systems containing sensitive or high-value data, often referred to as high-value assets (HVAs).
✅ Use Firewalls and Access Control Lists (ACLs) – Restrict communication between segments to only what is necessary.
✅ Apply the Principle of Least Privilege (PoLP) – Limit user and device access based on job roles and business needs.
✅ Regularly Test and Monitor Segmentation Policies – Ensure segmentation rules are enforced and adjust as needed.
✅ Combine Segmentation with Zero Trust – Assume no device or user should be trusted by default—verify access at every level.
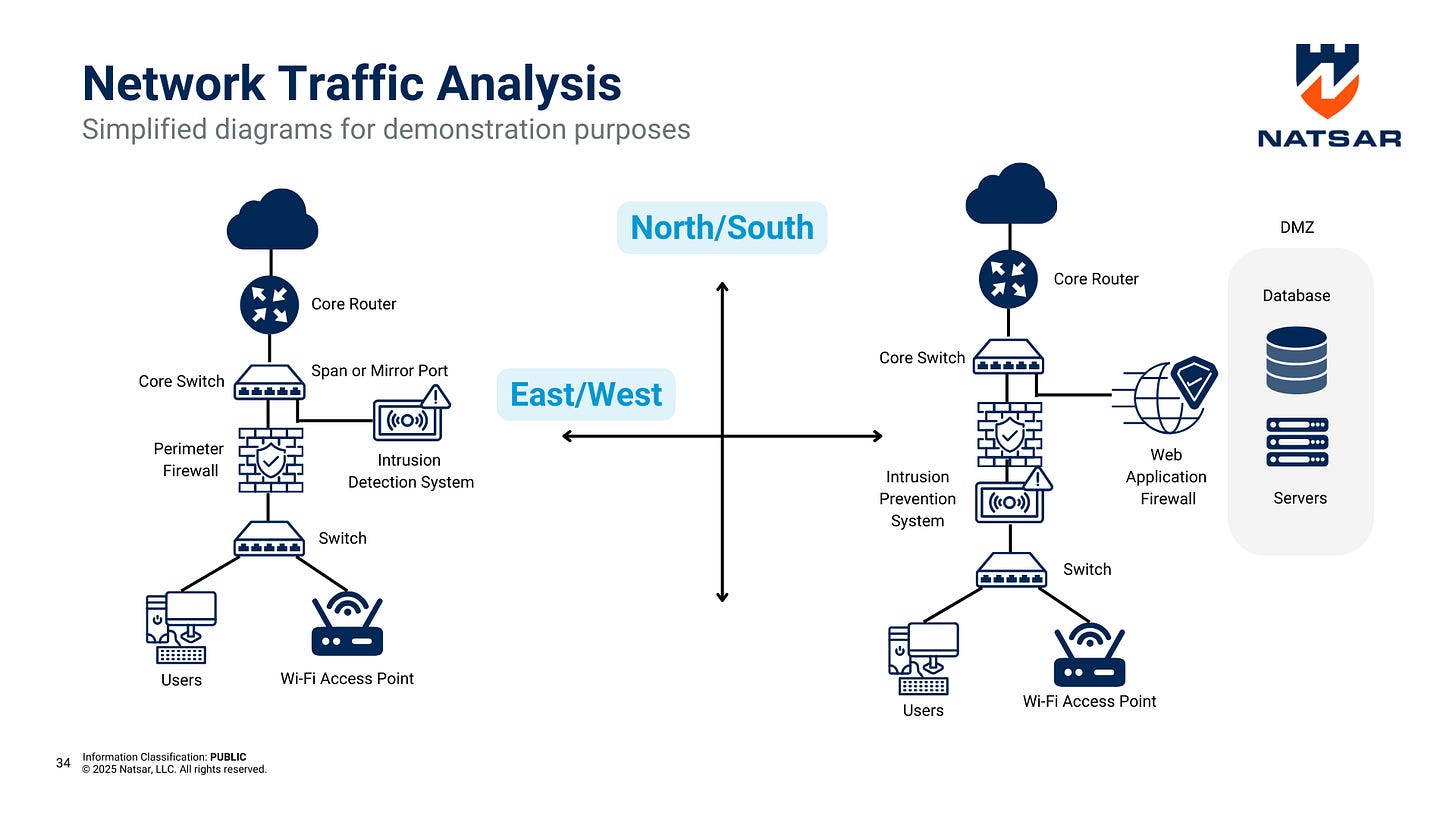
✅ Implement Network Monitoring Within Segments – Use next-generation firewalls (NGFW) and intrusion detection and prevention systems (IDPS) to monitor traffic within segmented environments, not just at the perimeter.
✅ Maintain Updated Network Diagrams – Detailed, regularly updated network diagrams are essential for troubleshooting, auditing, and verifying segmentation rules.
✅ Understand IP Addressing Schemes – Properly designed IP address allocations help enforce segmentation and simplify security monitoring.
Challenges and Considerations for Network Segmentation
While network segmentation significantly improves security, it is not easy to implement and requires careful planning. Organizations must consider:
Coordination and Planning – Effective segmentation requires collaboration across IT, security, compliance, and business units to ensure operational needs are met without compromising security.
Network Expertise – Designing and maintaining segmented networks demands a deep understanding of network architecture, IP addressing, firewall rules, and access control policies.
Troubleshooting Complexity – If not properly planned, segmentation can lead to unexpected connectivity issues, slowing down business operations.
Project Management – Segmentation projects require phased rollouts, extensive testing, and ongoing monitoring to ensure policies are correctly enforced.
Balancing Security with Usability – Over-segmentation can create bottlenecks, increase latency, and frustrate users if not designed with usability in mind.
Ongoing Maintenance – As organizations grow and technology evolves, segmentation policies must be regularly reviewed and updated.
Organizations that rush into segmentation without a solid plan risk breaking business-critical functions or leaving security gaps that attackers can exploit. A well-designed segmentation strategy is an investment, not just a one-time fix.
Bottom Line
Flat networks create significant security risks, allowing attackers to move freely and access critical data. Network segmentation is a fundamental cybersecurity strategy that limits lateral movement, protects high-value assets, and strengthens overall defenses. Just like a ship relies on watertight compartments to prevent sinking, your network needs segmentation to contain cyber threats and prevent widespread damage. While implementation can be complex, the security and performance benefits make it a necessary investment.
Learn More About Defense in Depth and Earn a Continuing Education Certificate
For a deeper dive into implementing Defense in Depth strategies, watch our no-cost training video, Introduction to Defense in Depth, available on YouTube or through Natsar’s website. Completing the training on Natsar’s website allows you to earn a certification for Continuing Professional Education (CPE) credits—ideal for cybersecurity professionals looking to enhance their expertise.
How Natsar Can Help
Natsar provides expert-led training and consulting services to help organizations implement Defense in Depth strategies effectively. Whether you need assistance with network security, zero trust, endpoint protection, or compliance, we offer customized solutions to strengthen your security posture.
Visit Natsar’s website to explore our training, cybersecurity assessments, and risk management solutions.



One of my current areas of work. Making our network more quantum and AI resistant. I would love to collaborate sometime.