Practical Patch and Vulnerability Management Strategies for Cybersecurity Risk Management
Actionable strategies for identifying, prioritizing, and addressing vulnerabilities to reduce cybersecurity risks.
Intended Audience: Beginner cybersecurity professional, business leaders, and anyone interested in enhancing their vulnerability and patch management programs.
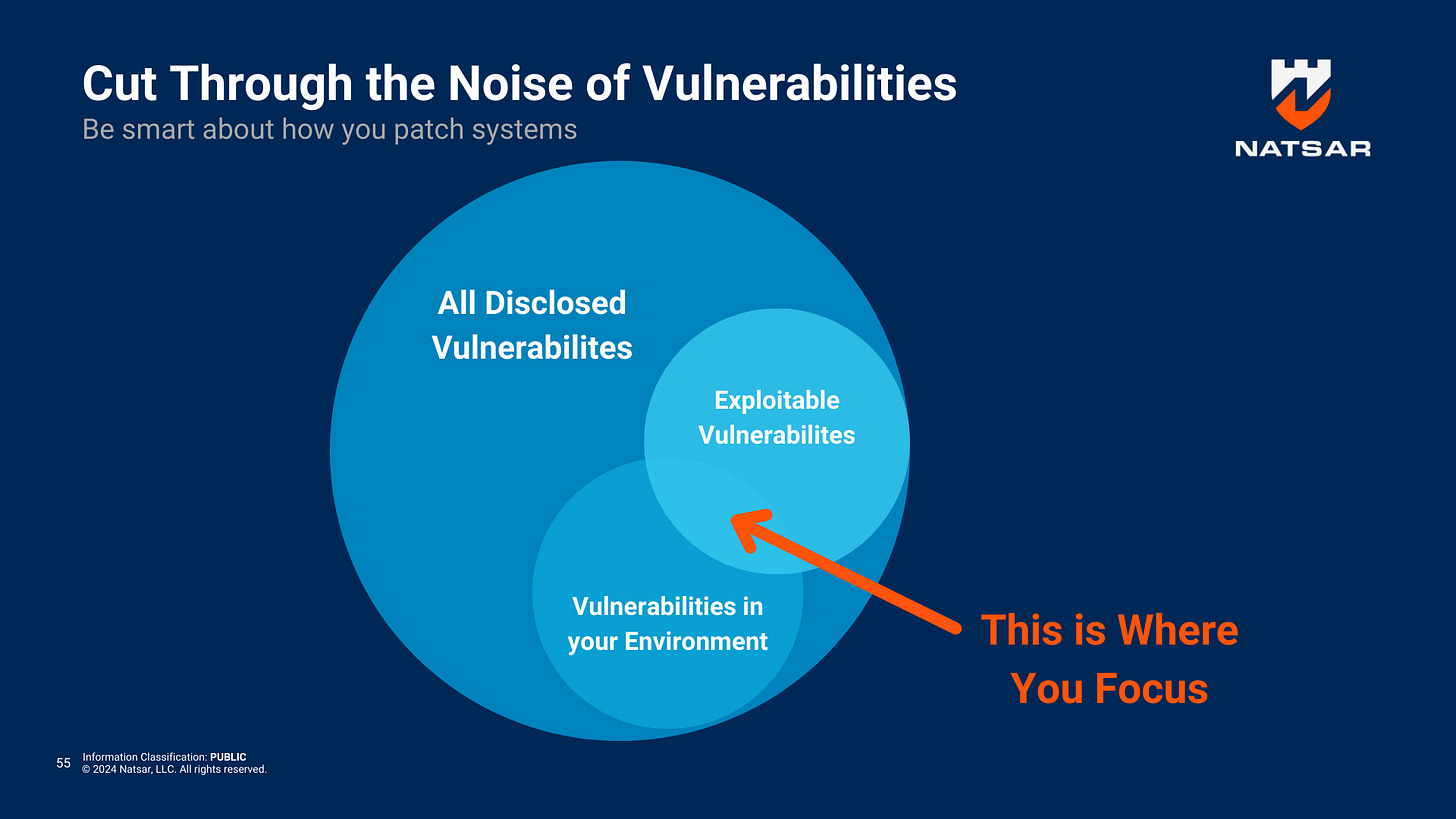
Effective cybersecurity risk management hinges on the ability to quickly identify, prioritize, and remediate vulnerabilities before they are exploited by attackers. While thousands of new vulnerabilities are disclosed each year, not all of them are equal—some pose minimal risk, while others represent critical threats that demand immediate attention. Understanding how to distinguish between these vulnerabilities and implement a structured approach to patch management is essential for safeguarding high-value assets.
In this post, we’ll explore key concepts in vulnerability and patch management, including how to assess risk using frameworks like the Common Vulnerability Scoring System (CVSS), the role of high-value assets in prioritization, and real-world insights on patching effectively in today’s complex threat landscape.
Understanding Vulnerabilities and Exploits
Not all vulnerabilities are created equal. A vulnerability represents a potential weakness in a system, but it only becomes truly dangerous when an exploit—an actual attack technique—can be used to take advantage of it.
Disclosed Vulnerabilities: Thousands of new vulnerabilities are disclosed each year, tracked by Common Vulnerabilities and Exposures (CVEs). However, only a fraction of these have known exploits.
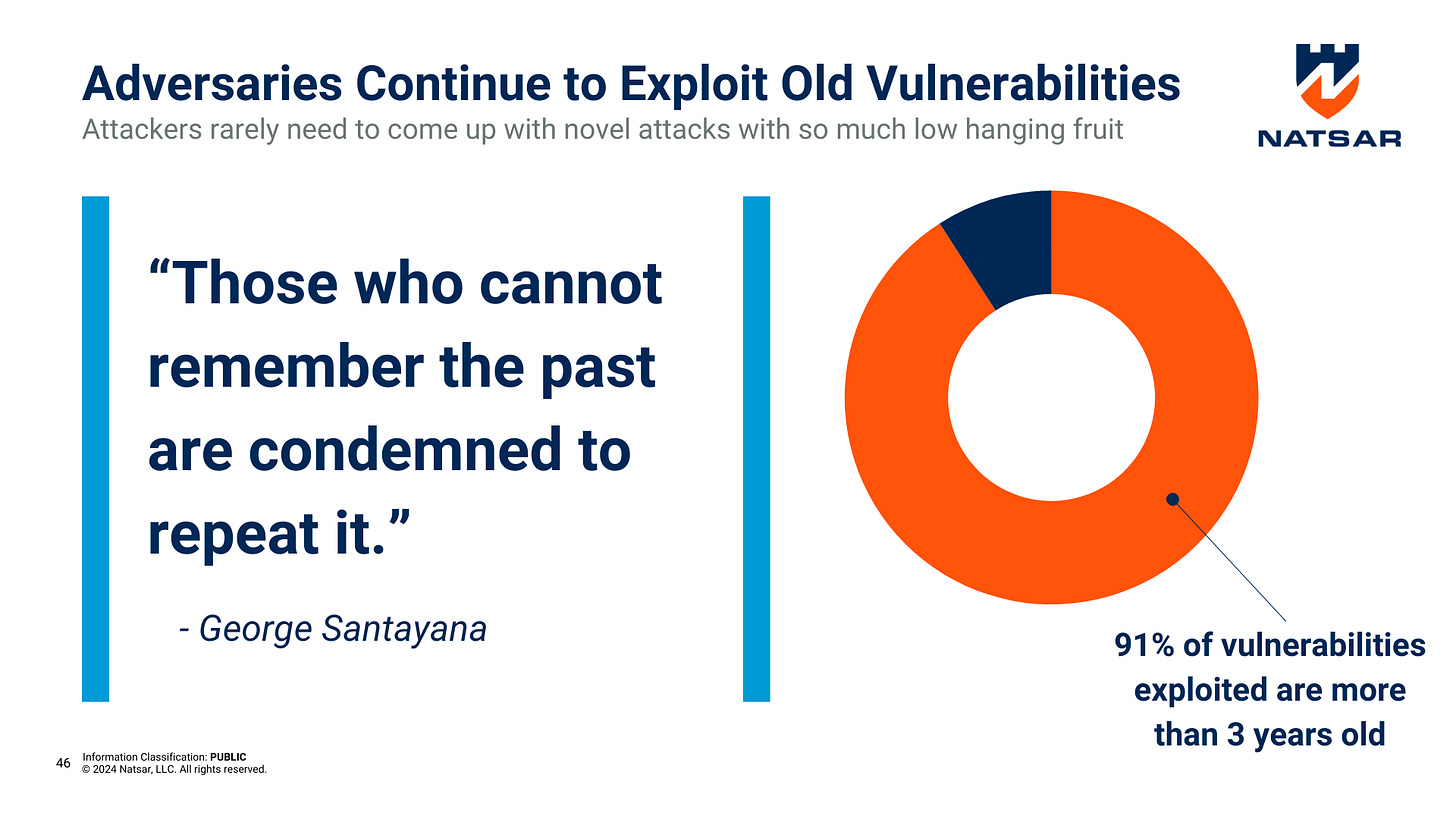
Exploitable Vulnerabilities: According to studies, a significant portion of attacks leverage vulnerabilities that are several years old. In fact, many exploited vulnerabilities have been known for an average of over three to five years before attackers weaponized them. This highlights a critical gap in patch management and risk prioritization.
By focusing on vulnerabilities with known exploits, organizations can better direct their limited resources toward patching the most dangerous flaws first.
The CISA KEV Catalog
The Cybersecurity and Infrastructure Security Agency (CISA) maintains the Known Exploited Vulnerabilities (KEV) Catalog, which lists vulnerabilities with active exploits. Unlike general vulnerability databases, the KEV catalog helps organizations zero in on high-priority patches by identifying vulnerabilities that are actively being exploited in the wild.
Leveraging resources like the CISA KEV ensures that cybersecurity teams aren’t overwhelmed by the sheer number of disclosed vulnerabilities but instead focus on those that represent real, immediate threats.
High-Value Assets and Prioritization
In patch management, not all assets are equally critical either. A vulnerability that might be low-risk in one environment could be devastating if it affects a high-value asset (HVA).
High-value assets (HVAs) are those systems, applications, or data that are crucial to the organization’s operations, reputation, or security. Examples include:
Systems that handle sensitive customer data (PII, PHI, etc.)
Critical operational technology (OT) systems in manufacturing or energy sectors
Core business applications that drive revenue
Prioritization Strategy:
Identify HVAs: Create an inventory of your organization’s most critical assets.
Map Vulnerabilities to HVAs: When a vulnerability affects an HVA, it should automatically be prioritized for patching.
Align with Business Impact: Always assess how a vulnerability could impact business continuity or regulatory compliance.

CVSS Scores and Their Limitations
The Common Vulnerability Scoring System (CVSS) provides a standardized way to rate the severity of vulnerabilities. Scores range from 0 to 10, with higher scores indicating more severe vulnerabilities.
However, relying solely on CVSS scores can lead to ineffective prioritization. Here’s why:
Context Matters: A vulnerability with a high CVSS score might not pose a significant risk if it doesn’t affect critical assets or lacks a known exploit.
Environmental Factors: CVSS doesn’t always account for the specific configurations and mitigations in place within your environment.
The Reality of Patch Management
Patch management isn’t just about applying updates—it’s about doing so in a way that minimizes business disruption while effectively reducing risk. Here are some key insights:
Patching Isn’t Always Immediate:
Patching requires testing and coordination to ensure it doesn’t introduce new issues. For critical systems, downtime can have significant business impacts.Operational Constraints:
Organizations often face challenges in patching due to operational requirements, legacy systems, or third-party dependencies.Average Age of Exploited Vulnerabilities:
Studies show that attackers often exploit vulnerabilities that have been publicly known for years. This means that while zero-day vulnerabilities grab headlines, the real risk often lies in failing to patch well-known issues.
Practical Patch and Vulnerability Management Strategies
Adopt a Risk-Based Approach:
Prioritize vulnerabilities based on their impact on HVAs, the likelihood of exploitation, and alignment with CISA KEV and CVSS scores.Automate Where Possible:
Use automated tools for vulnerability scanning, patch deployment, and reporting. Automation reduces human error and speeds up remediation efforts.Create a Patch Testing Process:
Establish a formal process to test patches in a controlled environment before applying them to production systems.Implement Patch Windows:
Schedule regular maintenance windows for applying patches. This ensures predictability and minimizes business disruption.Track and Report Progress:
Maintain a dashboard or report that tracks patching progress, especially for HVAs and KEV-listed vulnerabilities.
Bottom Line
Effective patch and vulnerability management isn’t about patching everything—it’s about patching what matters most and in the proper order. By understanding the difference between disclosed vulnerabilities and those with known exploits, prioritizing high-value assets, and using resources like the CISA KEV catalog, organizations can dramatically reduce their risk of cyberattacks. Pairing this with a structured patching process ensures that security improvements don’t come at the cost of operational stability.
Learn More About Risk Management and Earn a Continuing Education Certificate
For a deeper dive into cybersecurity risk management, watch our no-cost training video, Introduction to Cybersecurity Risk Management: A Practical Primer, available on YouTube or through Natsar’s website. By completing the training on Natsar’s website, you’ll not only gain valuable insights into risk management but also earn a certification for Continuing Professional Education (CPE) credits—perfect for professionals looking to advance their skills.
How Natsar Can Help
Natsar offers training and consulting services on managing cyber risks, creating in-depth risk, vulnerability, and threat assessments, briefing executives and boards, and ultimately helping organizations implement tailored risk management strategies that align with their business goals. Whether you need a comprehensive risk assessment or want to learn how to prioritize cybersecurity investments effectively, Natsar is here to help. Visit Natsar’s website to learn more.
In addition to our training, we also have products available to help you develop your risk management program.


