Getting Started with Configuration Management and System Hardening
Why creating standardized, secure system images is essential for protecting your organization from cyber threats
Intended Audience: Entry-level cybersecurity professionals, IT administrators, and anyone responsible for securing or developing systems.
Cybersecurity can feel overwhelming at first, especially when trying to secure numerous computers, servers, and devices. Attackers continuously look for vulnerabilities—ways to exploit outdated software, poorly configured devices, and common default settings. Thankfully, there’s a foundational cybersecurity approach designed to make this challenge significantly more manageable: configuration management and system hardening.
But what exactly does "configuration management" mean, and how do you practically "harden" a system? In this post, I'll clearly introduce these concepts and explain how they come together to strengthen your organization’s cybersecurity posture.
First, Why Do We Need Configuration Standards?
Every device—whether it’s a laptop, desktop, or server, comes from the manufacturer set to basic, default settings. These default settings are designed for ease-of-use, not security. They often include unnecessary features, open network ports, unused applications, or outdated software, all of which create vulnerabilities.
Attackers know about these default weaknesses, so the first step in cybersecurity is changing those defaults and implementing secure, standardized configurations across all your systems. This ensures every device has a strong baseline defense against known threats.
Organizations create configuration standards for several key reasons:
Reduce Vulnerabilities: Prevent attackers from exploiting default or weak configurations.
Consistency: Ensure every system has the same security settings, software versions, and configurations.
Simplified Management: Make it easier and faster to deploy, maintain, and troubleshoot systems.
Compliance and Auditability: Align configurations with regulatory requirements, industry standards, and best practices, simplifying compliance audits.
Creating a Secure Baseline: The Gold Disk Image
When creating secure configurations, the process usually begins by taking a basic or "vanilla" system—one with default settings, and carefully applying secure configurations. While many people immediately think about securing computers (such as Windows, Mac, or Linux systems), these principles equally apply to mobile devices, servers, and even network infrastructure such as routers and switches. Secure configuration baselines are also critical in cloud environments, which we’ll explore more deeply in a future post.
To begin this process, system administrators typically refer to trusted configuration baselines developed by cybersecurity industry experts, such as the Center for Internet Security (CIS) Benchmarks or the Defense Information Systems Agency’s Security Technical Implementation Guides (DISA STIGs). These benchmarks offer detailed guidelines and recommended settings proven to reduce security vulnerabilities. (We will cover these standards in much more depth in an upcoming post.)
Once the appropriate security baselines have been selected, system administrators install and configure the device exactly according to organizational requirements. This setup process includes configuring operating system security settings, installing and updating essential software, applying critical security patches, setting antivirus protections, configuring firewalls, and applying any customizations specific to the organization's needs.
Administrators often need additional time to test configuration changes thoroughly. Certain security settings might unintentionally disrupt essential business applications or legacy systems. While some settings might not be ideal from a strict cybersecurity perspective, operational requirements sometimes dictate these trade-offs. In these cases, administrators document accepted risks clearly, noting why certain less-secure configurations remain necessary.
After thorough testing and validation, IT teams create what's known as a gold disk image, also called a master or baseline image, using specialized imaging software. This image captures the entire configured system and serves as the organization's official standard. Going forward, all new devices are built from this gold disk image, and existing devices can be quickly rebuilt to this secure, approved baseline whenever needed.
Checking Your Work: Configuration Compliance Scans
Creating secure configurations and deploying gold disk images is an excellent start, but how do you know if your systems stay secure?
That’s where configuration compliance scanning tools come in:
Tools like CIS-CAT and Security Content Automation Protocol (SCAP) scanners can automatically compare your actual systems against the established benchmarks.
These scans quickly detect deviations, missing updates, or unauthorized changes, enabling your security team to quickly respond and fix issues.
Regular compliance scanning is crucial to maintaining security over the long term.
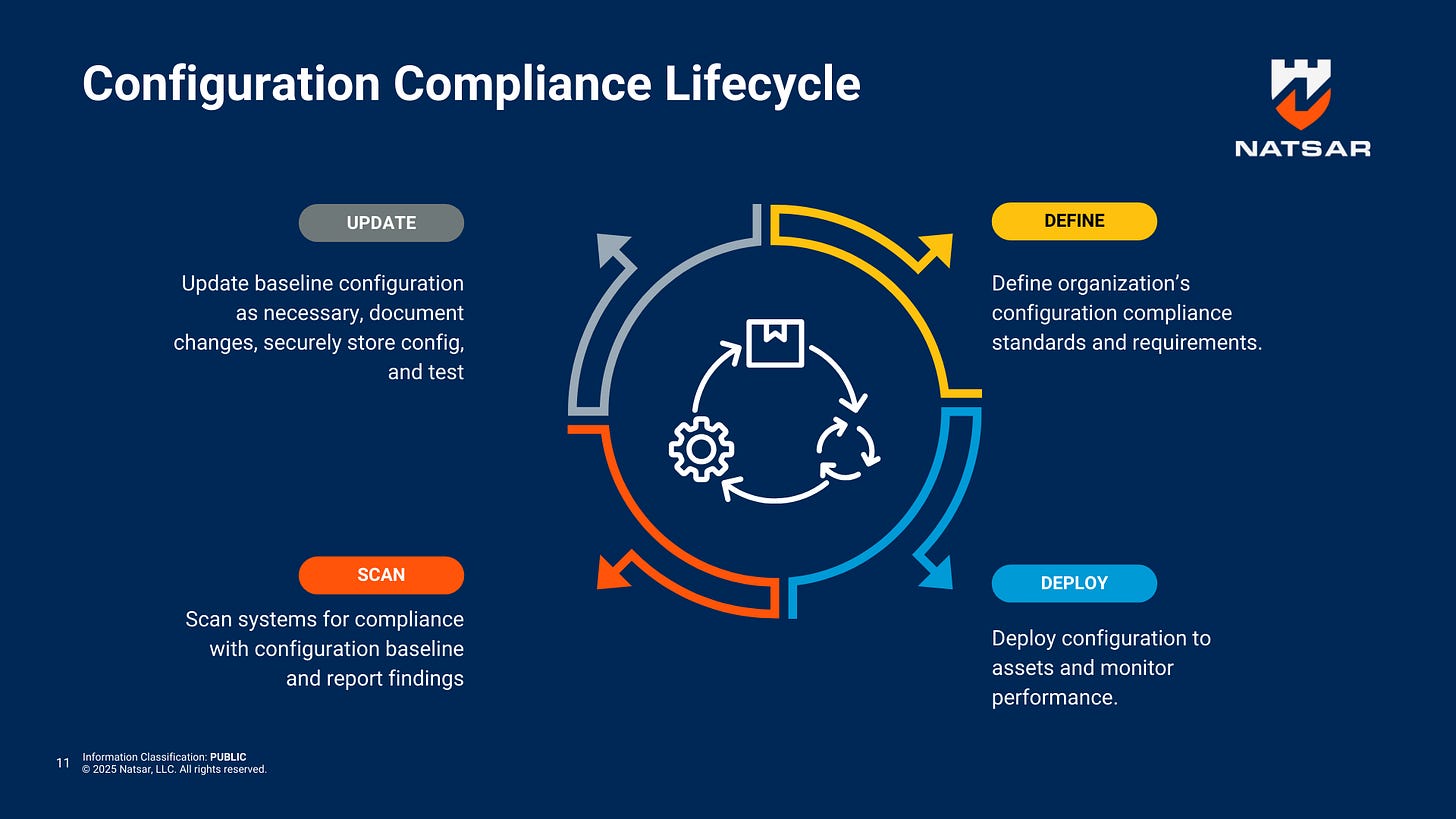
Maintaining Your Security Baseline
Secure configuration isn’t a one-time task, it’s an ongoing responsibility. Security configurations must be periodically reviewed and updated. Common maintenance activities include:
Regular Patching: Quickly apply patches and updates from vendors to address emerging vulnerabilities.
Configuration Audits: Periodically review system settings against established baselines to detect drift or unauthorized changes.
Benefits During Incident Response
Configuration management doesn’t just help prevent security incidents—it also greatly improves your ability to respond when incidents occur:
Faster Incident Detection: Deviations from your gold image stand out, helping security teams quickly identify compromised systems.
Rapid Recovery: You can swiftly restore compromised or infected systems using a known-good configuration.
Simplified Investigations: Known-good configurations help security investigators pinpoint unauthorized changes or malicious activities.
Challenges and Considerations
Configuration management and system hardening have clear benefits, but implementation requires effort and expertise:
Complexity: Creating and maintaining accurate gold images takes significant coordination and technical know-how.
Planning and Coordination: Ensuring all departments and business units have their needs met in a standard configuration requires careful planning and communication.
Expertise Required: Properly interpreting security benchmarks and applying them effectively requires experienced IT professionals.
Despite these challenges, the payoff in security, efficiency, and organizational resilience far outweighs the effort required.
Bottom Line
Establishing secure, consistent configurations through gold disk images and system hardening is one of the foundational strategies of cybersecurity. By taking a disciplined, standards-driven approach, organizations significantly improve their security posture, streamline IT operations, and respond more effectively when cyber incidents inevitably occur.
Learn More About System Hardening and Earn a Continuing Education Certificate
For a deeper dive into these concepts, watch my no-cost training video, Introduction to Configuration Management and System Hardening, available on YouTube or through Natsar’s website. By completing this training, you can earn Continuing Professional Education (CPE) credits and strengthen your cybersecurity skills.
How Natsar Can Help
Natsar provides cybersecurity consulting and advisory services for organizations large and small. Whether your organization needs help getting started, optimizing existing processes, or training IT staff, Natsar can support you at every step.
Visit Natsar’s website to learn more about enhancing your organization's cybersecurity resilience.
Stay Tuned for Our Next Post
In the next post, we’ll cover how to select and apply industry-standard configuration benchmarks effectively, making your security strategy even stronger.
If you found this helpful, please subscribe to Natsar Cyber Insights, follow us on social media, and share your thoughts in the comments section. Your engagement guides future content!




Great introduction to a foundational yet often overlooked area of cybersecurity. The breakdown of gold images and the value of configuration scanning tools was especially helpful.
Looking forward to the next post in the series!
Thank you very much, I'm glad you found the information helpful. Stay tuned for more content on this topic!