Critical Infrastructure (CI) Series, Post 4: Cyber Attack Kill Chain and How to Defend Against It
Breaking Down the Cyber Attack Kill Chain and Strategies to Stop Threats in Their Tracks
Intended Audience: Beginner, general public.
Every successful cyberattack follows a predictable series of steps—known as the cyber attack kill chain. Understanding this process is crucial for defenders, as it allows them to detect and disrupt attacks before they can cause harm. In this post, we’ll break down the key stages of the cyber attack kill chain and provide actionable strategies to stop attackers at each phase.
What is the Cyber Attack Kill Chain?
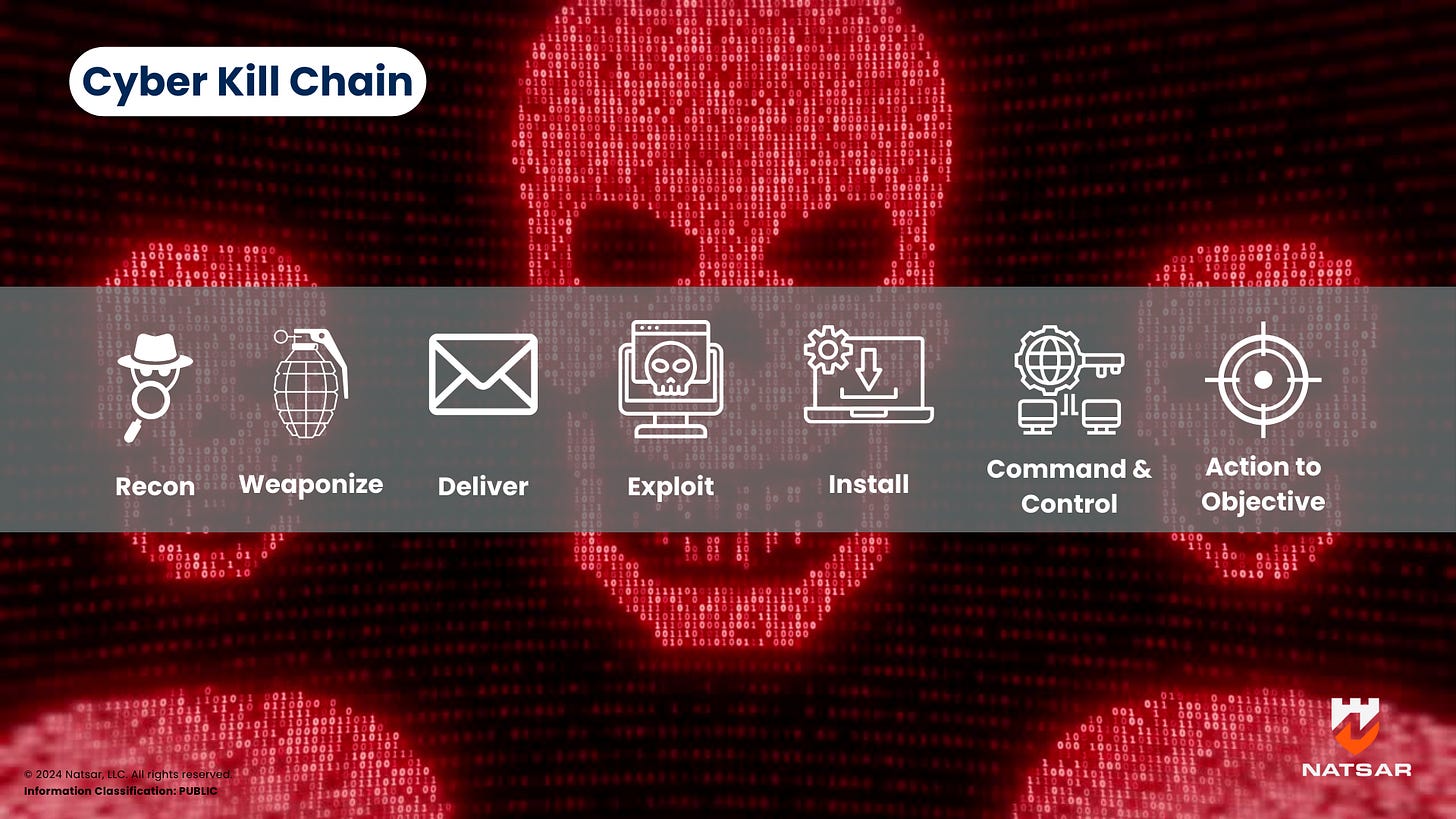
The cyber attack kill chain is a framework used to describe the typical stages of a cyberattack, from initial reconnaissance to achieving the attacker’s ultimate goal. By identifying these stages, organizations can focus their defenses on stopping attackers as early as possible.
Here are the main stages:
Reconnaissance
The attacker gathers information about the target, such as system vulnerabilities, employee details, and domain data, often through open-source intelligence (OSINT) tools.Weaponization
Based on their findings, the attacker develops or selects the tools they will use to exploit the target. This could include malware-laden emails or exploits targeting specific vulnerabilities.Delivery
The attacker delivers the payload, often via phishing emails, malicious links, or compromised USB devices. Phishing remains the most common method, accounting for over 90% of initial compromises.Exploitation
The attacker exploits a vulnerability or trick the victim into executing the malicious payload, granting them unauthorized access to the system.Installation
Malware or tools are installed to maintain persistence. Some modern attacks use non-persistent malware that operates in memory to avoid detection.Command and Control (C2)
The attacker establishes a communication channel with the compromised system, allowing them to issue commands and receive stolen data.Action on Objectives
Finally, the attacker achieves their goal, which could be stealing sensitive data, deploying ransomware, or disrupting operations.
Defending Against the Kill Chain
By addressing each stage of the kill chain, organizations can reduce the likelihood of a successful attack. Here’s how:
Disrupt Reconnaissance
Use tools to detect and block OSINT gathering attempts on your systems.
Implement domain privacy measures to limit publicly available information about your organization.
Prevent Weaponization
Patch known vulnerabilities to reduce the tools attackers can exploit.
Educate staff to recognize phishing attempts and suspicious files.
Harden Delivery Defenses
Deploy email filtering solutions to detect and block phishing attempts.
Use domain-based message authentication, reporting, and conformance (DMARC) to prevent spoofing.
Minimize Exploitation Opportunities
Conduct regular vulnerability assessments and penetration tests.
Apply least privilege principles to limit what attackers can access if they succeed.
Detect and Block Installation
Use endpoint detection and response (EDR) tools to identify malicious behavior in real-time.
Reboot systems regularly to remove non-persistent malware operating in memory.
Intercept Command and Control
Monitor network traffic for unusual outbound connections.
Use threat intelligence feeds to block known C2 servers.
Limit Action on Objectives
Encrypt sensitive data to make it unusable if stolen.
Regularly back up critical systems and test your ability to restore them quickly.
Why Early Detection is Critical
Stopping an attack early in the kill chain saves time, money, and reputation. A breach discovered at the reconnaissance or delivery stage is far less damaging than one detected after sensitive data has been stolen or systems crippled by ransomware.
Build a Resilient Defense Strategy
Aligning your defense strategy with a framework like the NIST Cybersecurity Framework (CSF) or CIS Controls can help ensure your organization is prepared for evolving threats. Regular risk assessments, employee training, and proactive monitoring are essential for staying ahead of attackers.
Bottom Line
The cyberattack kill chain outlines the sequential stages of a cyberattack, from reconnaissance to achieving the attacker’s objectives. By focusing on disrupting each phase—through measures like phishing defenses, vulnerability management, endpoint detection, and network monitoring—organizations can mitigate risks and prevent attackers from reaching their goals. Early detection is critical, as stopping an attack in its initial stages reduces damage, saves costs, and preserves trust. A proactive, layered defense strategy is essential to combat evolving cyber threats effectively.
Learn More About Defending Against the Kill Chain
For a deeper dive into the cyber attack kill chain and practical strategies to defend against it, watch my video, Securing Our Future: Defending Critical Infrastructure Against Cyberattacks, on Natsar’s website. By watching, you’ll earn Continuing Professional Education (CPE) credits while gaining actionable insights to protect critical systems.
Stay tuned for our next post in this series, where we’ll examine real-world case studies of critical infrastructure cyberattacks and the lessons learned.
How Natsar Can Help
Natsar specializes in helping organizations assess their vulnerabilities, strengthen their defenses, and develop effective incident response plans. Contact us today to learn how we can secure your systems against advanced threats.